Ransomware, and how to avoid it
Big ransomware attacks have been hitting the headlines, but these attacks can happen to users in your business, with potentially catastrophic results.
by Drew Aspland, 22nd February 2023
What is ransomware?
Ransomware is a type of malicious software (or malware) that is designed to encrypt the victim’s files or lock the victim out of their own system until a ransom is paid. It is a form of cyber extortion and can be extremely damaging to individuals and business organisations.
Ransomware typically infects a system through phishing emails, social engineering, or exploiting vulnerabilities in software. Once the malware has infected the system, it will start encrypting files or locking the user out of their system. The victim is then presented with a message that demands payment in exchange for the decryption key or unlocking of the system.
You may have heard of some of the more high-profile instances of ransomware in the UK. In 2017 the NHS was subject to the global WannaCry ransomware attack, causing widespread disruption to services, with many hospitals having to cancel appointments and procedures. The National Cyber Security Centre later attributed the attack to North Korean hackers.
And in January of this year, Royal Mail experienced a LockBit ransomware attack, leaving it unable to deliver parcels to international addresses. It emerged that a demand of £66million had been made to release their data, which Royal Mail refused to pay. It took weeks for Royal Mail to resume international deliveries.
These are just the big ones. Ransomware can effect anyone, and any business or organisation, big or small, including yours. Attacks have become increasingly common in recent years, and it’s important for you and your organisation to take steps to protect yourself.

How does ransomware infect a PC?
There’s more than a few ways you can fall victim to a ransomware attack, and you’ll notice they’re not too dissimilar to the ways you can fall for a phishing attempt or contract an old-school computer virus. Here’s the most common methods:
- Email attachments: they look like legitimate files, such as Word documents, PDFs, or ZIP files. Once the victim opens the attachment, the malware starts to do its thing.
- Malicious websites: Cybercriminals can use compromised or fake websites to spread their payload. These websites can contain exploit kits that take advantage of vulnerabilities in a web browser to install the malware.
- Software vulnerabilities: operating systems, applications, or plug-ins may all have unpatched vulnerabilities that can be exploited to gain access to a PC. Cybercriminals can use automated tools to scan for systems with unpatched loopholes and then deploy the malware.
- Social engineering: phishing emails, fake software updates or fraudulent ads can all be used as a vehicle for ransomware. These tactics are designed to trick the victim into clicking on a dodgy link or downloading a file.
Once their foot is in the door, it doesn’t take long to complete the attack. The malicious software quickly runs on the victim’s system, and begins to encrypt the victim’s files, rendering them inaccessible. The ransomware may also try to spread to other systems on the network.
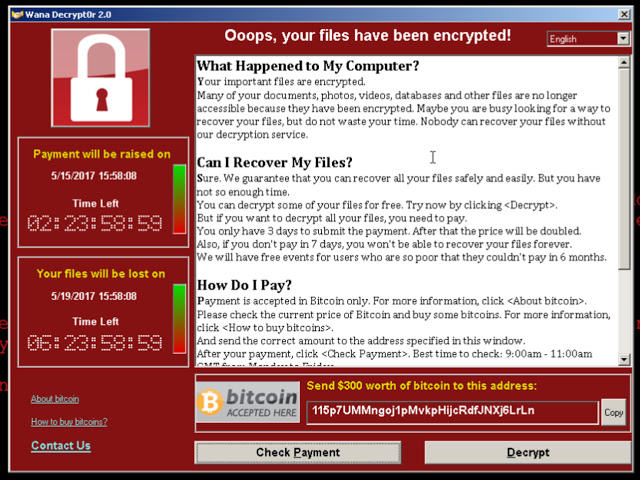
Before long, the victim will be presented with a message that demands payment (usually in Bitcoin) in exchange for the decryption key. The ransom note may also include a threat to delete the files permanently if the victim does not pay, or in the case of sensitive information, publish them. There is no guarantee that paying the ransom will result in the decryption of the files, and there’s an argument to be had that paying up will only encourage future attacks.
How can I tell if my machine is infected?
A big giveaway is if you are presented with a scary-looking message or ransom note on your computer screen. Such messages typically explain that your data has been encrypted, and that it will remain encrypted unless you pay a ransom. The message will tell you to buy an amount of Bitcoin, and will also direct you to pay this Bitcoin into a ‘wallet’, the address of which looks like a string of random letters and numbers. There may be images of skulls, and everything may be in blood red, to add to the seriousness of it all.
Beyond that, your files will no longer open, and the filenames may have been appended with file extensions like .encrypted or .locked, or had their extensions removed entirely. You may also experience random and frequent pop-up messages telling you that you have been infected. As you may have gathered, a ransomware infection is difficult to miss!
If you suspects that your machine is infected with ransomware, you should take immediate action to isolate the machine from the network (unplug the network cable or turn the wifi off) or turn the machine off entirely, and seek professional IT help. Do not pay the ransom, and do not engage in any kind of negotiation with the ransomers.
Can ransomware infect OneDrive, Google Drive, or Dropbox?
Yes. Cloud storage services like OneDrive and Google Drive synchronise files between the cloud and local devices, which means that any infected file stored locally on your PC will also be uploaded to the cloud, and potentially infect any other devices that also sync with that cloud storage account. This is why it’s incredibly important to disconnect the infected machine from the internet, as soon as you can.
Some of these cloud storage services offer what is called file versioning, which means you can turn back time on a file and restore it to a state of being from minutes, hours or days ago. But you should not rely solely on this.
How can I avoid ransomware?
Keep your software up to date. Make sure that your operating system, antivirus, and other software are all up to date. Software updates often include security patches that can prevent vulnerabilities that ransomware exploits. Nobody enjoys waiting for updates, but it could cost you your data, and in extreme situations, even your business.
Install reputable antivirus software and keep it up to date. Antivirus software can detect and prevent many types of malware, including ransomware. We recommend ESET or Sophos for business-grade antivirus and malware protection.
Be cautious when opening email attachments. Ransomware is often spread through malicious email attachments, so it’s essential to be cautious when opening emails from unknown senders. Don’t open any attachments that you weren’t expecting, and be especially wary of attachments with file types that are commonly used by malware, such as .exe, .vbs, and .scr. We have an article that explains phishing in depth here.
Don’t click on suspicious links. Avoid clicking on links in emails or on websites that look suspicious or untrustworthy. Instead, hover over the link to see the URL, and verify that it’s legitimate before clicking. If you don’t recognise the website or the domain, don’t click!
Regularly back up your data. Back up your important data to an external hard drive, cloud storage, or another secure location. This way, even if your PC is infected with ransomware, you won’t lose your critical data. We can advise on backup solutions for start-ups, small and medium businesses, or even if you’re working as a one-man band.
Use unique, strong passwords for all your accounts, and consider using a password manager to help you generate and manage your passwords. This can help prevent hackers from gaining access to your accounts and infecting your PC. We can recommend Dashlane, LastPass and Bitdefender.
And stay vigilant! All of the protection in the world cannot account for human error. If something looks, sounds and smells dodgy, it’s probably dodgy!
We help loads of businesses with their cybersecurity
If you’re concerned about the security of your business data, want to talk about how you can bring your business IT up-to-date, or just want to chat about how Plan IT Support can help you generally, get in contact using the form below, or call us on the number at the top of the page. We’ll keep it jargon-free, and there’ll be no obligation.